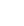WE GO BEYOND
By: Digicert, Inc
[class : 9] Computer Software; Computer Hardware; Computer Software For Providing Network, Internet, And Computer Security; Computer Antivirus Software; Internet And Data Security Software; Enterprise Security Software; Firewall Software; Computer Utility Software; Privacy Control Software; Content Filtering Software; Cloning Software, Namely, Software For Cloning Computer Hard Drives, Software For Cloning Computer Operating Systems, Software For Cloning Data Files, Software Reconfiguring Personal Computers; Computer Hardware Appliances That Provide Firewall, Content Filtering, Intrusion Alert, Virus Protection, Virtual Private Networking And Other Security Functions; Computer Software For Providing Online Identity Protection, Privacy Control, And Parental Control; Computer Software For Providing Intrusion Detection And Prevention; Computer Software For Scanning, Detecting, And Removing Viruses, Worms, Trojan Horses, Adware, Spyware, And Other Malware; Computer Software For Use In The Monitoring And Control Of Computer And Online Activity; Computer Software For Providing Online Transaction Security; Computer Software For Detection And Prevention Of Identity Theft And Fraud; Computer Optimization Software; Computer Software To Prevent, Diagnose And Repair Computer Problems; Computer Maintenance Software; Computer Software For The Creation Of Virtual Private Network; Computer Software For The Back-up, Storage, Restoration And Recovery Of Data, Folders, And Files; Computer Software For File Management And Transfer; Computer Software For Use In Updating Other Computer Software; Computer Application Software For Use In Electronic Storage Of Data, Documents And Receipts; Computer Application Software To Assist In Tracking, Managing, And Reporting Expenses, Credit Scores, Account Information, And Commercial Transactions; Computer Software For Connecting And Managing Remote Computers, For Synchronization Of Files Through E-mail, For Providing Security To Remote Computer Users, For Implementing Computer Software And Network Security Measures For Remote Computer Users; Computer Software, Namely, Encryption Software To Enable Secure Transmission Of Digital Information, Namely, Confidential, Financial And Credit Card Information Over The Internet, As Well As Over Other Modes Of Communication Between Computing Devices; Computer Programs For The Encryption And Authentication Of Electronic Information; Computer Software And Firmware For The Management, Transmission, And Storage Of Data And Information; Computer Software For Use In Networking Computers And Applications; Computer Software For Use In Monitoring Computers For Security Purposes; Computer Software In The Field Of Cryptographic Network Security And Data Security Functions; Downloadable User Manuals And Instructional Guides For Use In Connection With All Of The Foregoing; Downloadable Electronic Publications In The Nature Of Newsletters In The Fields Of Computer Software And Network Security.[class : 42] Monitoring Of Computer Systems For Security Purposes; Computer Services; Providing Information In The Fields Of Global Computer Network And Local Area Network Security, Preventing Computer Viruses; Computer Network Security And Internet Security Services; Computer Virus Protection Services; Identity Theft Protection Services, Namely, Fraud Prevention In The Form Of Personal And Financial Information Monitoring; Software As A Service (saas) Service Featuring Software For Personal Information Management, Software To Help Consumers Identify And Opt Out From Public Websites And Databases To Increase Privacy And Reduce Unwanted Solicitations, And Software For Fraud Protection And Identity Theft Prevention; Web Content Categorization And Filtering Services; Technical Support Services, Namely, Troubleshooting Of Problems With Computer Software And Computer Networks; Maintenance, Installation And Updating Of Computer Software For Others; Consulting Services For Others In The Field Of Computer Software, Computer Network Security And Internet Security; Computer Programming; Computer Software Design For Others; Leasing, Hire And Rental Of Computers, Computer Hardware, Computer Systems, Computer Programs And Computer Software; Providing Security Threat Management Systems, Namely, Monitoring And Tracking Of Malware, Security Vulnerabilities And Problems In Computer Software, The Internet, And Computer Networks; Computer Services Relating To Computer, Network And Internet Security, Including Content Screening And Filtering Services, Virus Scanning And Protection Services, Access Control Services, Authorization Management Services, Web Usage Monitoring Services, And Bandwidth Management And Protection Services; Notification And Delivery Of Software Updates; Development, Design, Implementation, Testing, Analysis, And Consulting Services In The Field Of Security, Access, Authorization, Authentication Encryption, And Identification Systems For Computers, Computer Hardware And Computer Networks; On-line Technical Support Services, Namely, Troubleshooting Of Computer Software Problems; Computer Consultation Regarding Computer Networks And Internal Computer Networks, Security Services For Computer Networks And Internal Computer Networks; Computer Consulting Services In The Field Of Security Integration, Network Security, Network Architecture, Encryption Technology, And Computer Security; Security Verification Of Computer Network Firewalls, Servers And Other Network Devices From Unauthorized Access, Namely, Analyzing Global Computer Information Network And Internal Computer Network Vulnerability; Provision Of Security Services For Virtual Private Computer Networks (vpns); Providing On-line, Non-downloadable Software For Computer And Internet Security Testing; Providing Consultants To Help Deploy, Supervise And Manage Information Technology Projects; Providing Information In The Field Of Information Technology Relating To Communications Devices, Computers, Computer Hardware, Computer Software, Computer Peripherals, And Computer Networks; Business Services In The Nature Of Managed Public Key Infrastructure (pki) Services, Namely, Application And Network Infrastructure Security Services; Providing Identity Verification Services In E-commerce Transactions; Fraud And Identity Theft Protection Services; Monitoring The Internet, Public Records, Credit Reports, Private And Public Electronic Databases, And Unregulated Global Computer Networks To Facilitate The Detection Of And Protection Against Identity Theft And Fraud; Computer Services, Namely, Data Recovery Services; Technical Support Services, Namely, Providing Back-up Computer Programs And Facilities; Consulting Services In The Field Of Design, Selection, Implementation And Use Of Computer Hardware And Software Systems For Others; Updating, Publishing And Maintenance Of Software For Networks And Standalone Computers In The Fields Of Security, Database Management, And Anti-virus Protection; Providing Online Database Regarding Computers, Computer Hardware, Computer Software, Computer Networks, Computer-related Services, Data Storage Management, Enterprise Information Management, And Online Analytical Processing (olap)
Trademark Details
This Brand Name WE GO BEYOND is applied by Digicert, Inc
This Trademark was applied on date 20 June 2017
This Application has been filed by their agent REMFRY & SAGAR
| Trademark | WE GO BEYOND |
| Application No | 3575225 |
| Filing Dte | 20-06-2017 |
| User Detail | Proposed to be used |
| Certificate Number | 2571020 |
| Valid Until | 20-06-2027 |
| Goods and Service | [class : 9] Computer Software; Computer Hardware; Computer Software For Providing Network, Internet, And Computer Security; Computer Antivirus Software; Internet And Data Security Software; Enterprise Security Software; Firewall Software; Computer Utility Software; Privacy Control Software; Content Filtering Software; Cloning Software, Namely, Software For Cloning Computer Hard Drives, Software For Cloning Computer Operating Systems, Software For Cloning Data Files, Software Reconfiguring Personal Computers; Computer Hardware Appliances That Provide Firewall, Content Filtering, Intrusion Alert, Virus Protection, Virtual Private Networking And Other Security Functions; Computer Software For Providing Online Identity Protection, Privacy Control, And Parental Control; Computer Software For Providing Intrusion Detection And Prevention; Computer Software For Scanning, Detecting, And Removing Viruses, Worms, Trojan Horses, Adware, Spyware, And Other Malware; Computer Software For Use In The Monitoring And Control Of Computer And Online Activity; Computer Software For Providing Online Transaction Security; Computer Software For Detection And Prevention Of Identity Theft And Fraud; Computer Optimization Software; Computer Software To Prevent, Diagnose And Repair Computer Problems; Computer Maintenance Software; Computer Software For The Creation Of Virtual Private Network; Computer Software For The Back-up, Storage, Restoration And Recovery Of Data, Folders, And Files; Computer Software For File Management And Transfer; Computer Software For Use In Updating Other Computer Software; Computer Application Software For Use In Electronic Storage Of Data, Documents And Receipts; Computer Application Software To Assist In Tracking, Managing, And Reporting Expenses, Credit Scores, Account Information, And Commercial Transactions; Computer Software For Connecting And Managing Remote Computers, For Synchronization Of Files Through E-mail, For Providing Security To Remote Computer Users, For Implementing Computer Software And Network Security Measures For Remote Computer Users; Computer Software, Namely, Encryption Software To Enable Secure Transmission Of Digital Information, Namely, Confidential, Financial And Credit Card Information Over The Internet, As Well As Over Other Modes Of Communication Between Computing Devices; Computer Programs For The Encryption And Authentication Of Electronic Information; Computer Software And Firmware For The Management, Transmission, And Storage Of Data And Information; Computer Software For Use In Networking Computers And Applications; Computer Software For Use In Monitoring Computers For Security Purposes; Computer Software In The Field Of Cryptographic Network Security And Data Security Functions; Downloadable User Manuals And Instructional Guides For Use In Connection With All Of The Foregoing; Downloadable Electronic Publications In The Nature Of Newsletters In The Fields Of Computer Software And Network Security.[class : 42] Monitoring Of Computer Systems For Security Purposes; Computer Services; Providing Information In The Fields Of Global Computer Network And Local Area Network Security, Preventing Computer Viruses; Computer Network Security And Internet Security Services; Computer Virus Protection Services; Identity Theft Protection Services, Namely, Fraud Prevention In The Form Of Personal And Financial Information Monitoring; Software As A Service (saas) Service Featuring Software For Personal Information Management, Software To Help Consumers Identify And Opt Out From Public Websites And Databases To Increase Privacy And Reduce Unwanted Solicitations, And Software For Fraud Protection And Identity Theft Prevention; Web Content Categorization And Filtering Services; Technical Support Services, Namely, Troubleshooting Of Problems With Computer Software And Computer Networks; Maintenance, Installation And Updating Of Computer Software For Others; Consulting Services For Others In The Field Of Computer Software, Computer Network Security And Internet Security; Computer Programming; Computer Software Design For Others; Leasing, Hire And Rental Of Computers, Computer Hardware, Computer Systems, Computer Programs And Computer Software; Providing Security Threat Management Systems, Namely, Monitoring And Tracking Of Malware, Security Vulnerabilities And Problems In Computer Software, The Internet, And Computer Networks; Computer Services Relating To Computer, Network And Internet Security, Including Content Screening And Filtering Services, Virus Scanning And Protection Services, Access Control Services, Authorization Management Services, Web Usage Monitoring Services, And Bandwidth Management And Protection Services; Notification And Delivery Of Software Updates; Development, Design, Implementation, Testing, Analysis, And Consulting Services In The Field Of Security, Access, Authorization, Authentication Encryption, And Identification Systems For Computers, Computer Hardware And Computer Networks; On-line Technical Support Services, Namely, Troubleshooting Of Computer Software Problems; Computer Consultation Regarding Computer Networks And Internal Computer Networks, Security Services For Computer Networks And Internal Computer Networks; Computer Consulting Services In The Field Of Security Integration, Network Security, Network Architecture, Encryption Technology, And Computer Security; Security Verification Of Computer Network Firewalls, Servers And Other Network Devices From Unauthorized Access, Namely, Analyzing Global Computer Information Network And Internal Computer Network Vulnerability; Provision Of Security Services For Virtual Private Computer Networks (vpns); Providing On-line, Non-downloadable Software For Computer And Internet Security Testing; Providing Consultants To Help Deploy, Supervise And Manage Information Technology Projects; Providing Information In The Field Of Information Technology Relating To Communications Devices, Computers, Computer Hardware, Computer Software, Computer Peripherals, And Computer Networks; Business Services In The Nature Of Managed Public Key Infrastructure (pki) Services, Namely, Application And Network Infrastructure Security Services; Providing Identity Verification Services In E-commerce Transactions; Fraud And Identity Theft Protection Services; Monitoring The Internet, Public Records, Credit Reports, Private And Public Electronic Databases, And Unregulated Global Computer Networks To Facilitate The Detection Of And Protection Against Identity Theft And Fraud; Computer Services, Namely, Data Recovery Services; Technical Support Services, Namely, Providing Back-up Computer Programs And Facilities; Consulting Services In The Field Of Design, Selection, Implementation And Use Of Computer Hardware And Software Systems For Others; Updating, Publishing And Maintenance Of Software For Networks And Standalone Computers In The Fields Of Security, Database Management, And Anti-virus Protection; Providing Online Database Regarding Computers, Computer Hardware, Computer Software, Computer Networks, Computer-related Services, Data Storage Management, Enterprise Information Management, And Online Analytical Processing (olap) |
| Business Name | Digicert, Inc |
| Business Type | Private Limited Company |
| Business Sector | Service |

What trademarKing.in Does
TrademarKing help you to register trademark in India. Every year many business use TrademarKing.in to register & protect their brands with smooth filing process. TrademarKing also monitors your Brand name if TrademarK Registration is done through TrademarKing.in. Now you can Register TrademarK Through TrademarKing.in.
In India we have filed 100000+ Trademark Registration , so start now! to register your trademark.
TrademarKing is a free trademark search engine developend by PCNR Trademarks Management Pvt Ltd, India.
Trademark Monitoring